Human-plus-AI solutions mitigate security threats
Fifty years ago, the average business transaction was pretty straightforward. Shoppers handed purchases directly to cashiers, business partners shook hands in person, and people brought malfunctioning machines to a repair shop across the street. The proximity of all participating parties meant that both customers and businesses could verify authority and authenticity with their own eyes.
But the internet has changed the very nature of how we transact, and more recently the rise of remote work has added yet more complexity to the mix. Today, a customer in Texas can call a business in Prague for product support and reach a technician ten thousand miles away in a coworking space in India—all while using a communication platform on the cloud. In other words, there are many more technology layers and much greater distances involved in even basic business interactions today. As such, authentication and verification have become much more challenging.
This greatly expanded attack surface can spell bad news for companies that aren’t properly equipped to defend themselves against cybersecurity threats. Globally, the average data breach costs $4.35 million. In the U.S., the figure is more than double that—around $9.44 million. And such breaches are all-too-common occurrences, with more than 1,800 data compromises reported in the U.S. in 2022.
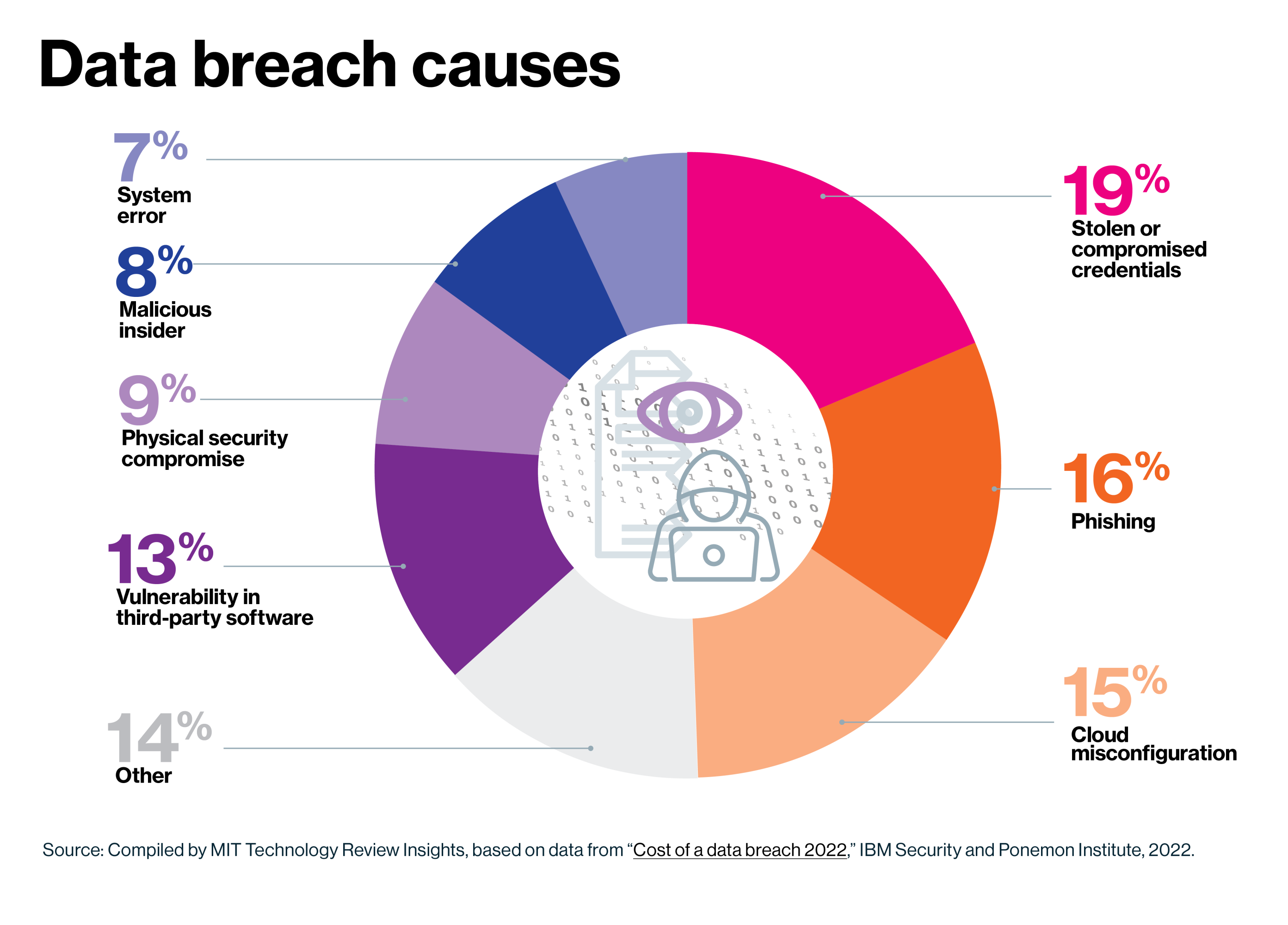
But in the same way that business has evolved for the modern era, protective cybersecurity measures are also becoming more advanced. Today, digital solutions that integrate emerging technologies like AI into human-centric workflows are helping mitigate myriad threats. What’s more, intelligent digital solutions can protect sensitive business data while simultaneously simplifying and streamlining business operations.
Download the full report.
This content was produced by Insights, the custom content arm of MIT Technology Review. It was not written by MIT Technology Review’s editorial staff.


